Initial Analysis
To begin the analysis of the EasyPass application, we first need to download and unzip the necessary files. We can achieve unzipping by using the following command in the terminal:
unzip Find\ The\ Easy\ Pass.zip #hackthebox
Once the files are unzipped, we discover an executable file named EasyPass.exe. To gain more insight into its nature, we can employ the file command:
file EasyPass.exe
The command reveals that EasyPass.exe is a PE32 GUI application designed for Intel-based Windows systems. In an attempt to extract useful information, we can use the strings command on the executable and filter the output for any mentions of “PASS” or other likely strings:
strings EasyPass.exe | grep PASS
Unfortunately, this search does not yield any significant results.
Debugging and Dissasembly
Given that EasyPass.exe is an executable file, we can proceed to analyse it using OllyDbg, an interactive debugger for Windows. By running EasyPass on a Windows 10 virtual machine created for analysis only, we can explore the executable’s behaviour without concerns about potentially damaging the system.
Now we can open the exe in OlyyDB (run as admin), and perform a search for all referenced text strings
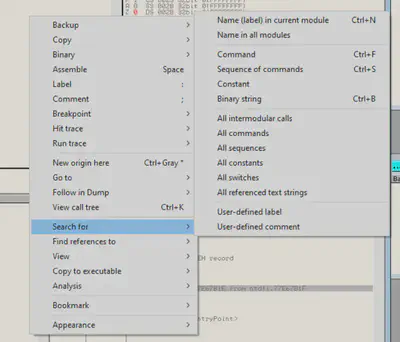
By examining the code, we determine where the “Wrong Password” message originates from. To gain further insights, we can follow the reference in the disassembler:
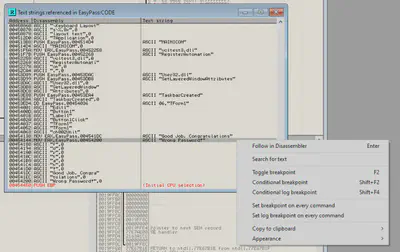
From here we can search for references to the address to see where the previous instruction was:
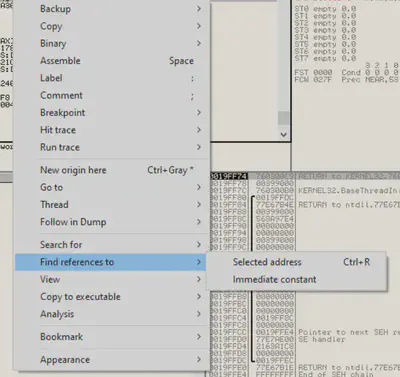
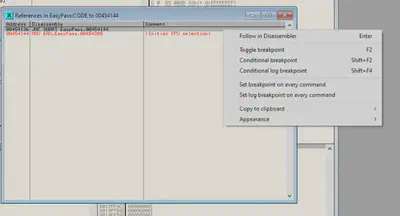
Since nothing directly references this point, we can assume the previous call was the preceding address, which is a function call. To gather more information, we can set a breakpoint at this address::
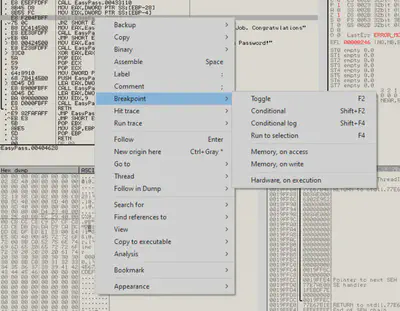
With the breakpoint in place, we can execute the program by clicking the play icon at the top. To trigger the breakpoint, we enter an incorrect password during the execution. Subsequently, we can inspect the registers to gather relevant data:
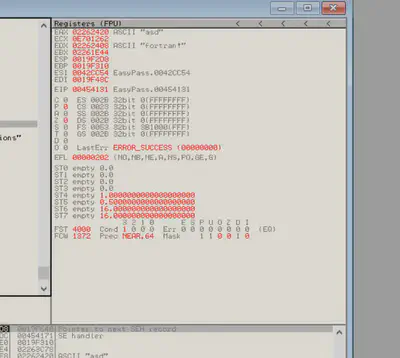
Upon examining the register values captured during the conditional check, we notice that the password I entered was “asd,” which suggests that “fortan!” might be the correct password. To verify this assumption, we can rerun the program, input the password, and it grants us access to the flag.